BaFin requirements for monitoring systems AMLA
BaFin requirements for monitoring systems AMLA: The requirements for monitoring systems are specified in Chapter 6 of the interpretation notes of the BaFin special section for credit institutions. These interpretative notes also have an impact on other obliged entities within the meaning of the AMLA.
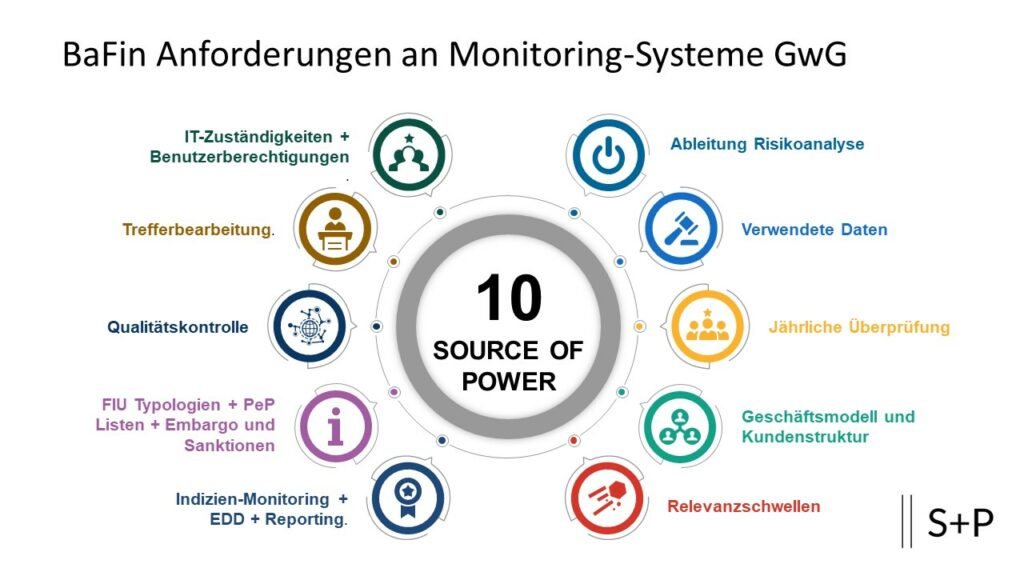
What requirements does BaFin place on the adequacy of monitoring systems for money laundering prevention?
# 1: Is it possible to derive it from the risk analysis?
# 2: Which data are included in the monitoring?
# 3: Has the annual review been carried out and documented?
# 4: Is the system sufficiently geared towards the bank-specific business activities and the customer structure? Have adjustments been documented in an audit-proof manner?
# 5: Has the appropriateness of the established relevance thresholds been comprehensibly justified?
# 6: Does the software used meet the requirements for evidence monitoring, EDD and evaluation functions?
# 7: Does the software cover the FIU typologies, PeP lists, sanction and embargo lists? Are these lists updated regularly?
# 8: Is there evidence of quality control?
# 9: Is there an audit-proof, traceable documentation of the hit processing?
# 10: Have the following responsibilities been established?
BaFin requirements for monitoring systems AMLA
When it comes to the selection and nature of the AMLA monitoring systems, BaFin has the following requirements:
# 1: Is it possible to derive it from the risk analysis?
The decision as to which data processing system is used and which types of business and transactions are to be examined in more detail on the basis of the rule-based indicators, scenarios or parameters set previously, depends on the scope of the business activity and on the findings of the institution-specific risk analysis of the respective credit institution.
The assessment parameters used, when a situation is to be assessed as unusual in relation to comparable cases, must be defined on the basis of the institution-specific risk situation (cf. Section 6 (1) sentence 2 of the GwG).
# 2: Which data are included in the monitoring?
The data processing system used is to be supplied with the relevant data from the relevant IT systems, ie above all payment and transaction systems, and the bank’s customer master databases.
# 3: Has the annual review been carried out and documented?
Every payment transaction – internal, external, or transitory – must always be checked by the system. However, certain case constellations can be ruled out if there are no money laundering risks to the contrary.
- This is regularly the case for internal bookings for the bank’s own purposes without customer reference.
- It must be ensured that the exclusions are documented in an audit-proof manner and checked for appropriateness at least once a year .
The personal responsibility of the money laundering officer and the board of directors for the fulfillment of the obligation according to § 43 GwG remains unaffected.
# 4: Is the system sufficiently geared towards the bank-specific business activities and the customer structure? Have adjustments been documented in an audit-proof manner?
In order to detect potentially conspicuous business relationships, transactions or account movements, the system must be geared towards the bank-specific business activities and the customer structure of the bank .
- The parameters must always be adjusted to the individual risk situation of the credit institution or the institution’s own risk analysis if the risks identified in the risk analysis are not adequately covered by existing indicators.
- An adjustment can also consist in the deactivation of certain parameters.
- Adjustments to the parameters must be documented in an audit-proof manner.
The data processing system as a whole must be correct, complete and up-to-date in terms of data, consistency, topicality and interfaces. The supply systems as a whole must also be correct, complete and up-to-date in terms of data, consistency, timeliness and interfaces.
The data processing system must display the generated hits in full (see Section 6 (1) sentence 2 of the GwG).
# 5: Has the appropriateness of the established relevance thresholds been comprehensibly justified?
If the data processing system weights the indications, the credit institution has to set an appropriate relevance threshold from which transactions are to be regarded as suspicious and are displayed by the system.
IT-based decisions of the data processing system must be explainable and comprehensible. The essential influencing factors for the system and the generated hits must be able to be shown and the occurrence of the hit result must be plausible ( prohibition of black boxes ).
In the case of missing data, the missing values must be clearly marked and promptly replaced with real data. Until the data has been replaced, risk-sensitive default values (“replacement values”) must be set.
The data processing system must be supplied with the historical data relevant to the individual indicators and scenarios.
Suitability of the software as a monitoring system AMLA + BaFin Requirements for monitoring systems AMLA
# 6: Does the software used meet the requirements for evidence monitoring, EDD and evaluation functions?
The software used for the data processing systems is particularly suitable if they
- basically enables the credit institution to recognize transaction patterns , anomalies and deviations ,
- contains an indication model that enables individual configurations,
- in addition to customer and product risks, also country risks (e.g. use of current country risk lists ) and terrorist financing risks ( e.g. use of current embargo and sanction lists; the use of different software for the data processing systems with regard to money laundering, other criminal acts and terrorist financing as well as sanction monitoring is permitted),
- with the entirety of the evidence used, includes aspects of money laundering prevention , the prevention of terrorist financing and – if necessary – the prevention of other criminal acts ,
- adequately covers the increased risks within the meaning of Section 15 (3) of the GwG,
- the checking of names for similarities by means of fuzzy search logic („fuzzy logic“) as part of the sanction screening and
- Contains or is supported by evaluation and statistical functions that enable the bank to carry out ad hoc research and to use evaluations for regular updating and further development of the risk analysis.
- Evaluation and statistics functions can also be located outside the data processing systems.
The BaFin requirements for monitoring systems AMLA also require the implementation of Section 15 (3) AMLA in ongoing monitoring. Section 15 (3) of the GwG regulates the following requirements:
In particular, there is a higher risk when it is
- a contractual partner of the obliged entity or a beneficial owner is a politically exposed person, a family member or a person known to be closely related,
- is a business relationship or transaction in which a third country identified by the European Commission in accordance with Article 9 Paragraph 2 of Directive (EU) 2015/849, which has been amended by Article 1 number 5 of Directive (EU) 2018/843, has a high Risk or a natural or legal person resident in this third country is involved; this does not apply to branches of obliged entities established in the European Union according to Article 2 Paragraph 1 of Directive (EU) 2015/849, which has been amended by Article 1 No. 1 of Directive (EU) 2018/843, and for majority owners of these Subsidiaries located in the obliged entity that are located in a third country with a high risk,
- is a transaction that compares to similar cases
a) is particularly complex or unusually large,
b) follows an unusual transaction pattern, or
c) has no obvious economic or lawful purpose, or
- for obliged entities according to Section 2 (1) numbers 1 to 3 and 6 to 8 it is a cross-border correspondence relationship with respondents domiciled in a third country or, subject to an assessment by the obliged entity as an increased risk, in a country of the European Economic Area.
# 7: Does the software cover the FIU typologies, PeP lists, sanction and embargo lists? Are these lists updated regularly?
The data processing systems used must cover relevant typologies in the area of money laundering, combating terrorism and other criminal acts in their settings, rules and indicators, taking into account the risk situation of the respective credit institution , in order to be able to recognize conspicuous customer relationships or transactions.
In addition, they must present suitable scenarios that at least reflect the current findings and publications of the FIU and are based on further publicly available knowledge about money laundering, terrorist financing and other criminal acts.
- The use of all the legal requirements imaging lists, especially sanctions lists , embargo lists and PEP lists , must be ensured by the data processing systems.
- All lists must be checked and updated on an ad-hoc or regular basis. The possibility of peer group comparisons (especially with large customer groups) should be used if it is suitable.
Functionality of the data processing systems as AMLA monitoring systems
# 8: Is there evidence of quality control?
The correctness and up-to-dateness of the indicators, rules, threshold values, scores and risk classification systems must be checked regularly and on a case-by-case basis, paying special attention to all relevant legal changes, regulatory requirements, warnings and information.
- Significant changes in the institute’s risk analysis must be taken into account in the calibration of the monitoring system.
- Regular professional maintenance , overhaul and – if necessary – technical upgrading of the hardware of the data processing system to ensure its functionality must take place.
The smooth cooperation of the individual components and their interfaces to the data processing systems must be guaranteed ( end-to-end ).
The credit institute has to continuously check the correct functionality of the data processing systems and is also responsible for regular quality control of the data processing systems by an independent auditor .
- This quality control can take place as part of the annual audit.
- In the event of a malfunction or failure of the data processing system, the bank must take into account the emergency concept in accordance with AT 7.3 of MaRisk.
Changes to the legal requirements with regard to the use of data processing systems and their subject matter must be implemented immediately after they come into force.
Proper and secure documentation of the AMLA monitoring systems
# 9: Is there an audit-proof, traceable documentation of the hit processing?
The indications, rules, scenarios, calibrations, users, their authorizations and corresponding changes as well as the hits and their processing including the planned further procedure (e.g. filing a suspicious transaction report to the FIU) must be documented in a reasonable time for a knowledgeable third party and in the sense of Section 8 of the GwG.
- The documentation of the processing of hits must reflect the content-related discussion of the individual case.
- Changes to the documentation are only permitted if they are recognizable as such and the corresponding responsibilities can be traced.
- In addition, a reason and the time for such a change must be documented in a comprehensible manner for a knowledgeable third party.
Management, staff and consultants – these requirements apply to AMLA monitoring systems
# 10: Have the following responsibilities been established?
It must be ensured that IT authorizations are assigned to data processing systems in accordance with AT 7.2 of MaRisk.
- This has to show which people are involved in the processing and administration (including testing and checking) of the data processing system.
- The persons equipped with access authorizations (including external consultants) must have the necessary professional qualifications and the necessary expertise. AT 7.1 No. 2 is relevant.
The money laundering officer is responsible for the technical further development of the data processing system, in particular for changing the existing indicators, rules or scenarios, threshold values and scores as well as their generation and calibration and must have the relevant knowledge.
- The technical implementation can be carried out by specialized employees from other internal or external units or service providers.
- Employees entrusted with the use of the data processing system must be adequately trained.
In addition, professional training is required in the event of significant changes , such as the generation of new indicators or scenarios.
Responsibilities are to be defined for
- IT administrator: user permissions
- Central body: calibration for risk management
- Interfaces to the data processing systems ( end-to-end ): external data providers